Think Cybersecurity Compliance is Boring? Think Again!
Data breaches and cyberattacks have become all too common, the importance of cybersecurity compliance cannot be overstated.
Imagine your personal information falling into the wrong hands, or your company's confidential data being exposed to hackers - a terrifying thought! But fear not, for cybersecurity compliance is here to save the day.
It's like having a shield of protection around your digital assets, ensuring that you meet the necessary standards and regulations to keep cyber threats at bay.
Compliance may sound like a boring bureaucratic term, but in cybersecurity, it's the superhero cape that safeguards organizations from unseen dangers lurking in cyberspace.
From financial institutions to healthcare providers and even small businesses, everyone needs to play by the rules when it comes to protecting sensitive information. So buckle up as we dive into the fascinating world of cybersecurity compliance - where complex regulations meet cutting-edge technology to create a secure digital environment for us all.
What is Cybersecurity Compliance?
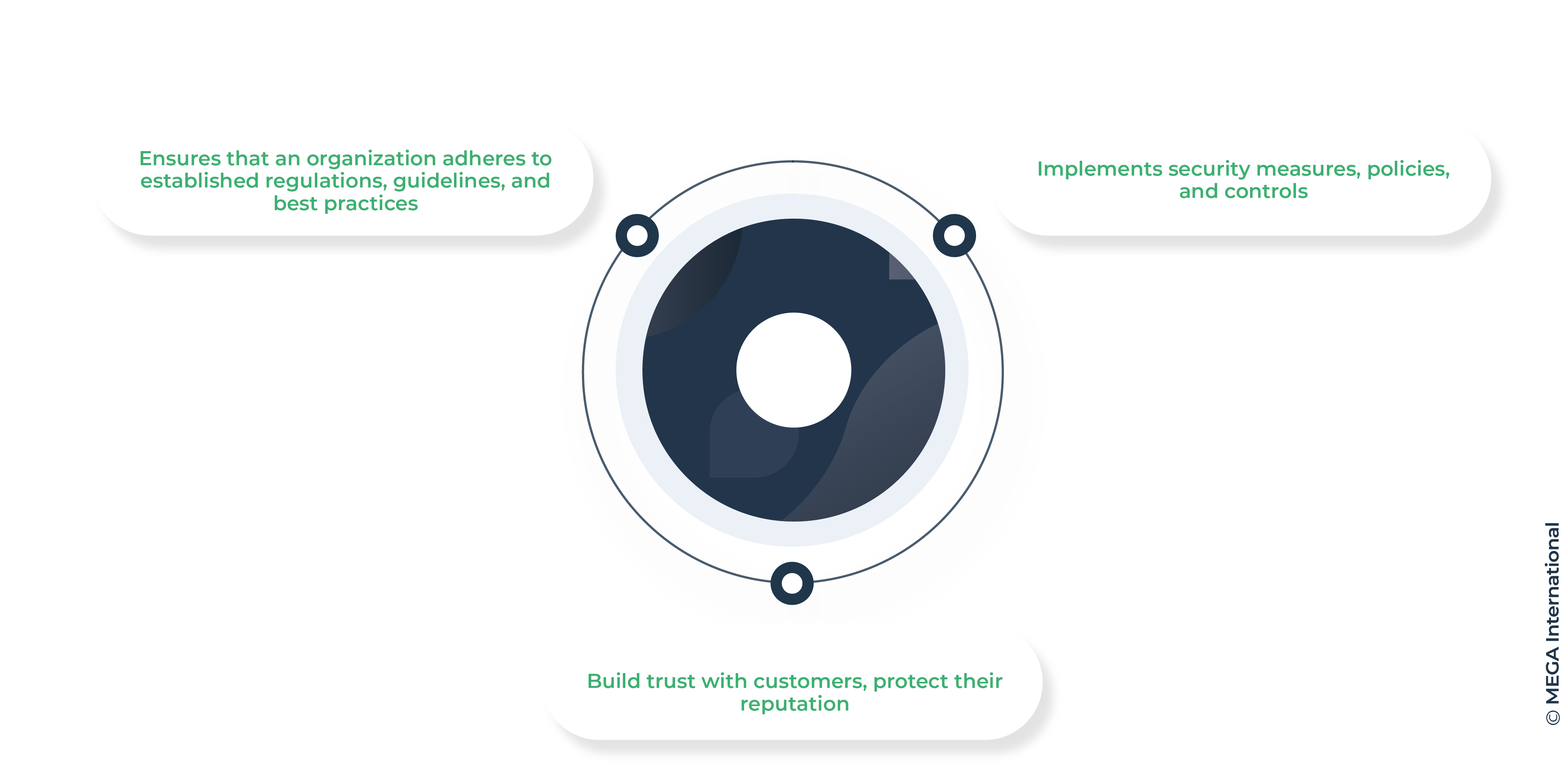
Cybersecurity compliance refers to the process of ensuring that an organization adheres to established regulations, guidelines, and best practices to protect its digital assets from cyber threats. It involves implementing security measures, policies, and controls to safeguard sensitive data and mitigate the risk of cyberattacks.
Compliance requirements can vary depending on the industry and location of the organization, with mandates such as GDPR, HIPAA, PCI DSS imposing specific cybersecurity standards.
Non-compliance with cybersecurity regulations can result in severe consequences for organizations, including financial penalties, reputational damage, and legal action. Additionally, failure to meet compliance requirements leaves businesses vulnerable to data breaches and other security incidents that can have far-reaching consequences.
Therefore, maintaining cybersecurity compliance is crucial for organizations looking to build trust with customers, protect their reputation, and stay ahead in today's rapidly evolving threat landscape.
Overview of Major Cybersecurity Regulations
Several key cybersecurity regulations govern how organizations should protect their data. These include the General Data Protection Regulation (GDPR) in the European Union, the Health Insurance Portability and Accountability Act (HIPAA) in the United States, and the Payment Card Industry Data Security Standard (PCI DSS). Each regulation sets forth specific requirements for data protection, breach notification, and risk management.
How to Achieve Cybersecurity Compliance
Achieving cybersecurity compliance can seem like a daunting task, but with the right strategies in place, it can be manageable and effective. One key aspect to consider is implementing regular security assessments to identify vulnerabilities and patch them promptly. This proactive approach not only helps in meeting compliance requirements but also strengthens your overall security posture.
Steps to implement cybersecurity compliance
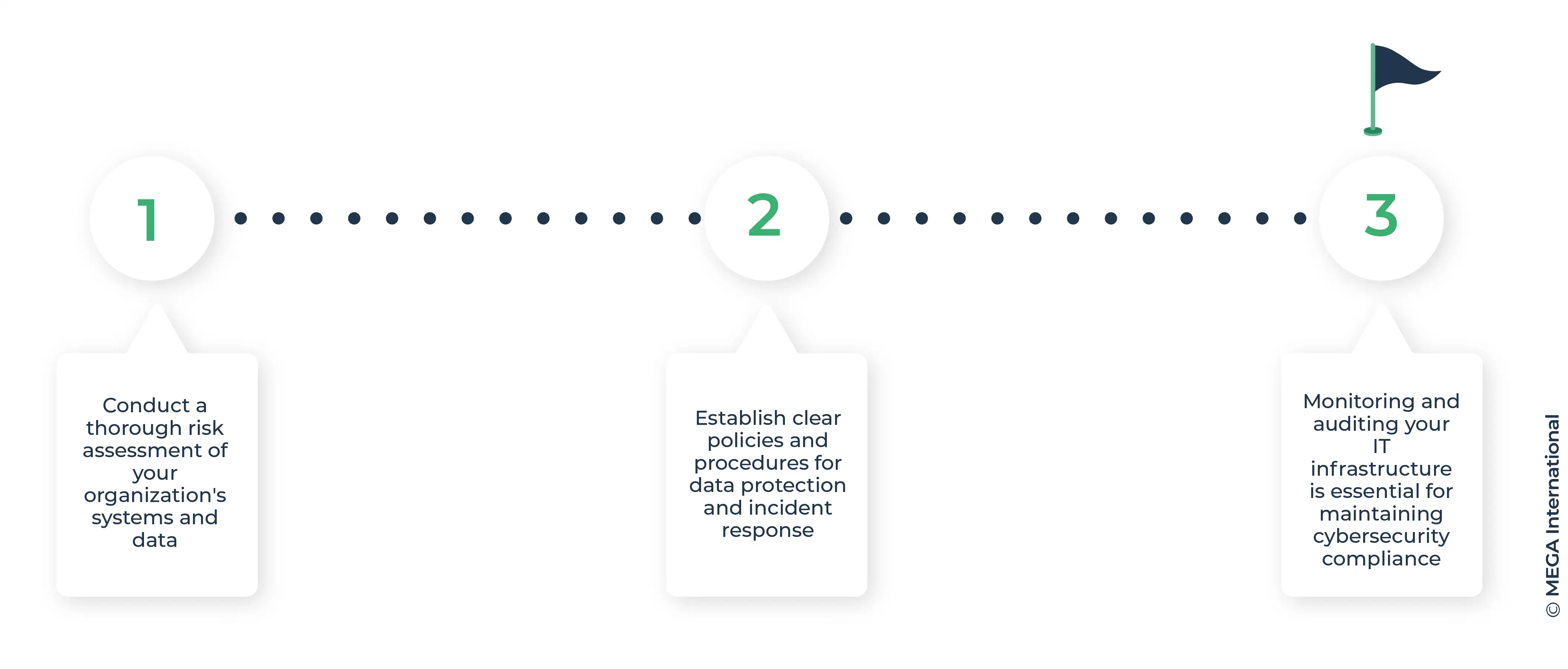
One crucial step in implementing cybersecurity compliance is to conduct a thorough risk assessment of your organization's systems and data. By identifying potential vulnerabilities, you can prioritize security measures and allocate resources effectively. This proactive approach ensures that your cybersecurity strategy is tailored to address specific threats and risks unique to your business operations.
Another important step is to establish clear policies and procedures for data protection and incident response. By outlining guidelines for access control, data encryption, and regular system updates, you can create a framework that promotes a culture of cybersecurity awareness within your organization. Training employees on these policies will also help reinforce the importance of cybersecurity compliance at all levels of the company.
Lastly, regularly monitoring and auditing your IT infrastructure is essential for maintaining cybersecurity compliance.
Conducting routine assessments of security controls, performing penetration testing, and staying informed about emerging threats are crucial steps in adapting your cybersecurity strategy to evolving risks.
You can better protect your organization from potential cyberattacks by staying vigilant and proactive in assessing and addressing vulnerabilities.
How to Establish a Cyber Security Compliance Program?
A compliance program is the backbone of any organization striving to meet legal obligations and uphold ethical standards.
The multifaceted nature of modern business requires a comprehensive approach to compliance, integrating various components to create a cohesive and effective strategy.
The importance of a compliance program cannot be overstated, as it not only safeguards the organization from legal repercussions but also enhances its reputation and operational efficiency.
Components of a Cybersecurity Compliance Program
Leadership and Governance
Effective leadership and governance are crucial to the success of a cybersecurity compliance program. Board oversight ensures that cybersecurity is a priority at the highest level, while compliance committees facilitate focused discussions and actions on cybersecurity issues. Leadership commitment sets the tone for the entire organization, emphasizing the importance of adhering to cybersecurity standards and regulatory requirements.
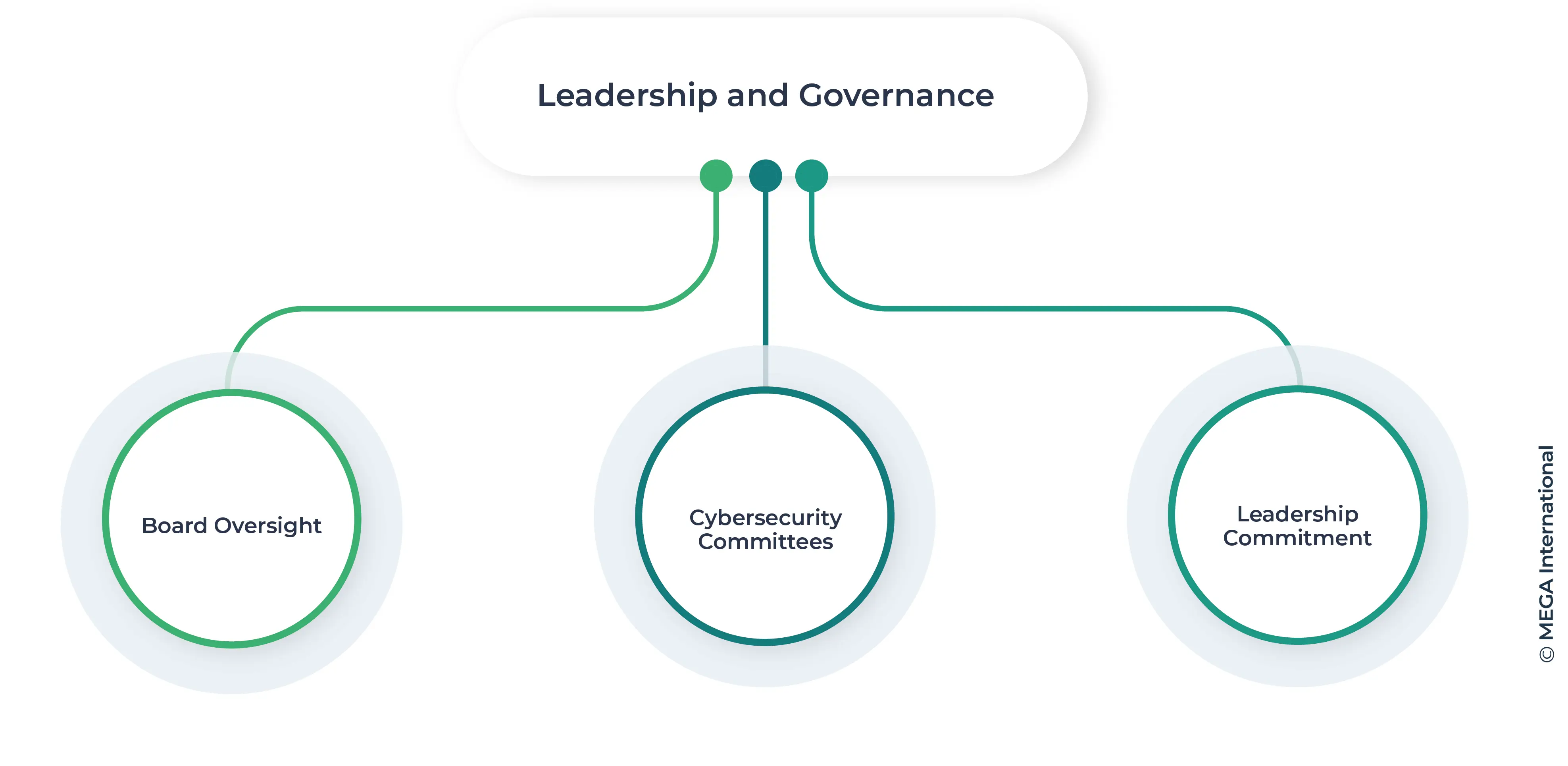
- Board Oversight: The board of directors plays a pivotal role in overseeing the cybersecurity compliance program, ensuring it aligns with the organization's strategic goals and risk appetite. Regular reviews and updates from the Chief Information Security Officer (CISO) keep the board informed and engaged.
- Cybersecurity Committees: Establishing committees dedicated to cybersecurity helps address specific areas of concern, promote cross-functional collaboration, and ensure comprehensive coverage of all cybersecurity aspects.
- Leadership Commitment: The involvement and commitment of senior leaders are essential in driving the importance of cybersecurity throughout the organization. Their support ensures that cybersecurity is integrated into the corporate culture.
Policies and Procedures
Well-defined policies and procedures form the foundation of a cybersecurity compliance program. They provide clear guidelines on acceptable behavior and operational standards, ensuring all employees understand their responsibilities.
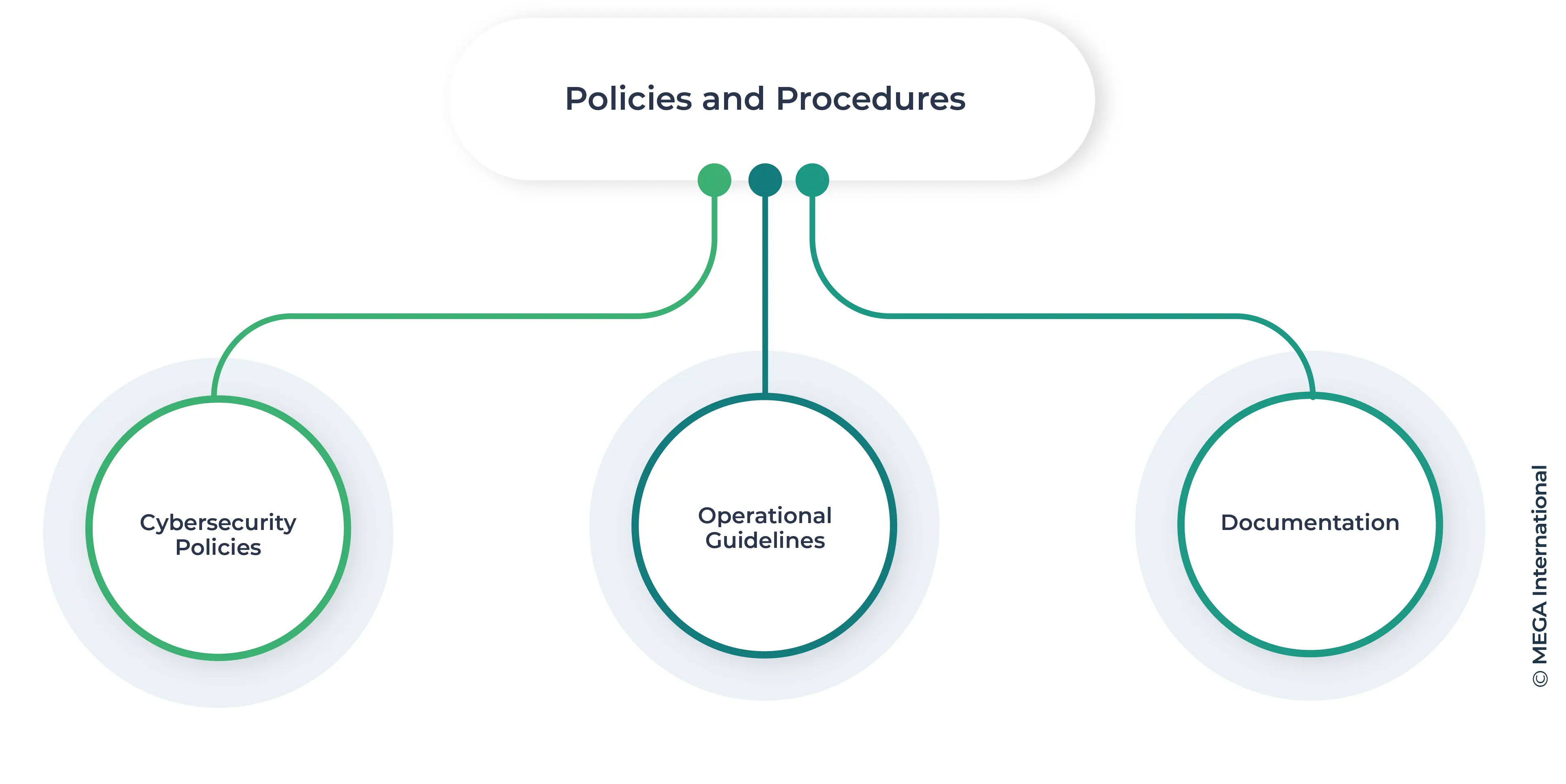
- Cybersecurity Policies: Robust cybersecurity policies outline the principles and standards that govern the organization's cybersecurity practices. They serve as a reference point for decision-making and behavior.
- Operational Guidelines: Detailed operational guidelines offer step-by-step instructions on performing tasks in compliance with cybersecurity requirements. These guidelines help maintain consistency and reduce the risk of non-compliance.
- Documentation: Proper documentation of cybersecurity policies and procedures is crucial for transparency and accountability. It ensures that employees can access the necessary information and refer to it as needed.
Training and Education
Ongoing training and education are vital for maintaining an effective cybersecurity compliance program. Employees must be well-informed about cybersecurity requirements and equipped with the skills to adhere to them.
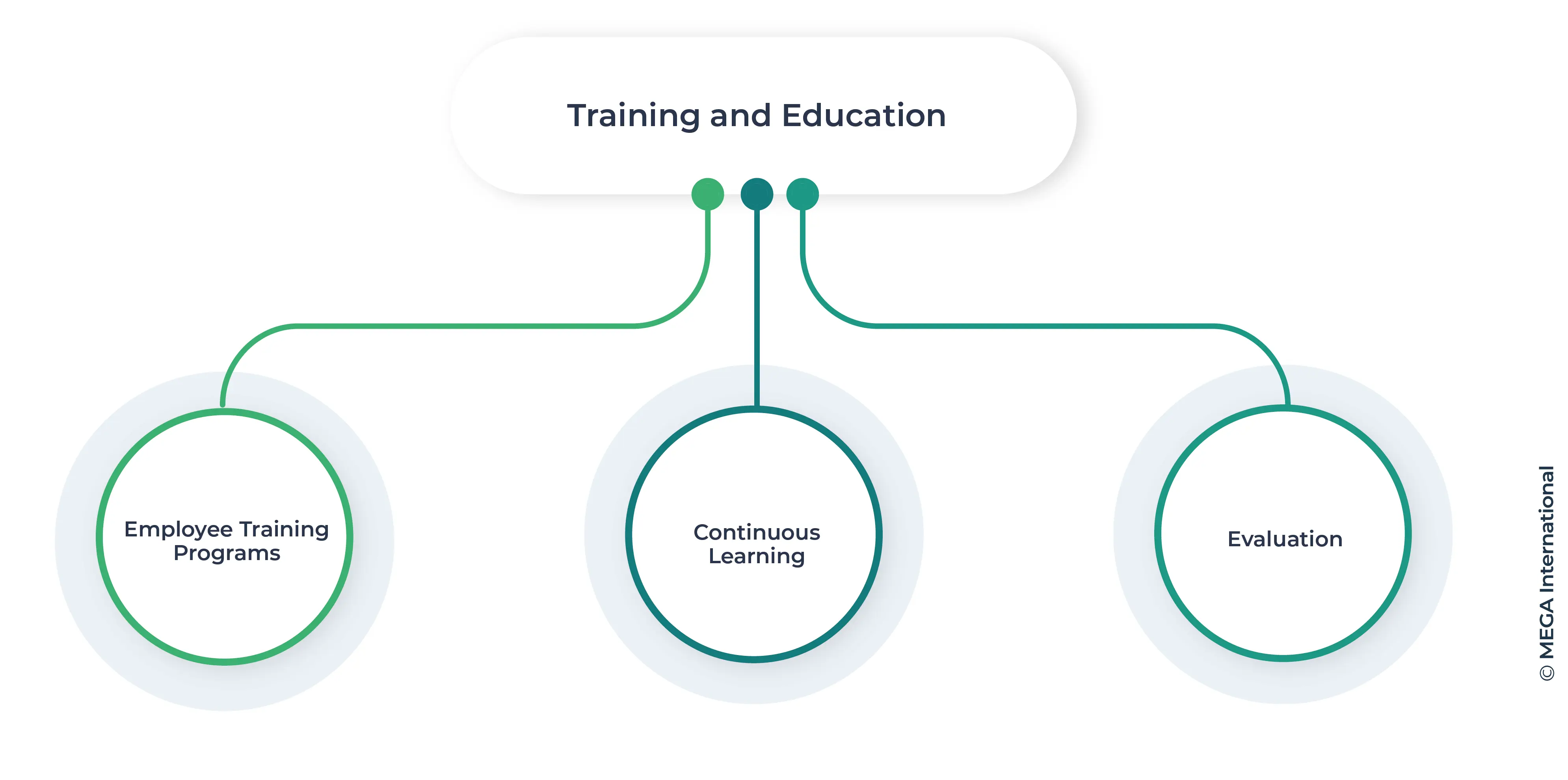
- Employee Training Programs: Regular training sessions help employees stay updated on cybersecurity policies, regulations, and best practices. Interactive training methods, such as workshops and e-learning modules, enhance engagement and retention.
- Continuous Learning: Encouraging a culture of continuous learning ensures that employees remain informed about changes in cybersecurity regulations and industry standards. This can be achieved through periodic updates and refresher courses.
- Evaluation: Assessing the effectiveness of training programs is crucial for identifying gaps and areas for improvement. Feedback from participants and performance assessments provide valuable insights.
Risk Assessment and Management
Identifying and managing risks is a core component of a cybersecurity compliance program. A proactive approach to risk assessment helps mitigate potential issues before they escalate.
- Identifying Risks: Conducting thorough risk assessments involves identifying potential cybersecurity risks across various areas of the organization. This includes evaluating internal processes and external factors.
- Risk Mitigation Strategies: Developing strategies to mitigate identified risks is essential for preventing non-compliance. This may involve implementing controls, revising procedures, or enhancing training programs.
- Continuous Monitoring: Regular monitoring and review of risk management efforts ensure that the organization remains vigilant and responsive to emerging risks.
Monitoring and Auditing
Continuous monitoring and auditing are essential for maintaining the integrity of a cybersecurity compliance program. They provide a mechanism for detecting and addressing issues in a timely manner.
- Internal Audits: Conducting regular internal audits helps identify compliance gaps and areas for improvement. Audits should be systematic and cover all relevant areas of the organization.
- External Audits: Engaging external auditors provides an objective assessment of the cybersecurity compliance program. External audits offer a fresh perspective and can uncover issues that internal teams may overlook.
- Continuous Improvement: The findings from audits should be used to drive continuous improvement. This involves addressing identified issues, implementing corrective actions, and refining processes.
Reporting Mechanisms
Effective reporting mechanisms are crucial for encouraging transparency and accountability within the organization. They provide a channel for employees to report cybersecurity concerns and incidents without fear of retaliation.
- Whistleblower Policies: Establishing clear whistleblower policies protects employees who report cybersecurity misconduct or compliance violations. It ensures that their concerns are taken seriously and addressed promptly.
- Anonymous Reporting Systems: Providing anonymous reporting options encourages employees to come forward with information without fear of reprisal. This can be facilitated through hotlines, online platforms, or suggestion boxes.
- Incident Response: A structured incident response process ensures that reported issues are investigated thoroughly and addressed appropriately. Prompt response to incidents helps mitigate potential damage.
Enforcement and Discipline
Enforcement and discipline are necessary to uphold the integrity of the cybersecurity compliance program. Consistent application of disciplinary measures reinforces the importance of compliance and deters non-compliant behavior.
- Disciplinary Procedures: Clear disciplinary procedures outline the consequences of non-compliance. These procedures should be fair, transparent, and consistently applied.
- Enforcement Policies: Developing enforcement policies ensures that disciplinary measures are proportionate to the severity of the violation. It also provides a framework for addressing repeated offenses.
- Consistent Application: Ensuring that enforcement policies are applied consistently across the organization helps maintain fairness and credibility. It demonstrates that cybersecurity compliance is taken seriously at all levels.
Response and Prevention
A proactive approach to response and prevention helps address cybersecurity compliance issues effectively and prevent future occurrences. This involves a thorough investigation of incidents and the implementation of corrective actions.
- Investigation Processes: A structured investigation process ensures that cybersecurity violations are investigated thoroughly and objectively. It includes defining roles, gathering evidence, and documenting findings.
- Corrective Actions: Implementing corrective actions based on investigation findings helps address the root causes of cybersecurity issues. This may involve revising policies, enhancing training, or improving controls.
- Prevention Strategies: Developing prevention strategies focuses on identifying potential cybersecurity risks and taking proactive measures to mitigate them. This can include conducting regular risk assessments and implementing preventive controls.
Technology and Tools
Leveraging technology and tools enhances the efficiency and effectiveness of a cybersecurity compliance program. Advanced tools facilitate compliance management, data analysis, and automation of routine tasks.
- Compliance Management Software: Utilizing compliance management software streamlines cybersecurity processes, centralizes documentation, and facilitates real-time monitoring.
- Data Analytics: Data analytics tools help identify cybersecurity data trends, patterns, and anomalies. This enables organizations to make informed decisions and respond to emerging risks.
- Automation Tools: Automation tools reduce the burden of manual cybersecurity tasks, such as data entry and reporting. They enhance accuracy and free up resources for more strategic activities.
Third-Party Management
Managing third-party relationships ensures vendors and partners adhere to cybersecurity standards. This involves conducting due diligence and monitoring third-party activities on an ongoing basis.
- Vendor Risk Management: Assessing and managing risks associated with vendors and third parties helps prevent compliance breaches. This includes evaluating their cybersecurity programs and performance.
- Third-Party Compliance: Ensuring third parties comply with regulatory requirements and organizational standards is essential for cybersecurity compliance. This can involve contractual agreements and regular audits.
- Due Diligence: Conducting thorough due diligence before engaging with third parties helps identify potential cybersecurity risks. This includes background checks, financial assessments, and reference checks.
Ethical Culture and Environment
Promoting an ethical culture and environment fosters a commitment to cybersecurity compliance and integrity. It involves engaging employees and demonstrating the organization's dedication to ethical behavior.
- Promoting Ethics: Encouraging ethical behavior involves integrating ethical principles into everyday operations. This can be achieved through training, communication, and leadership by example.
- Leadership Role: Leaders play a critical role in shaping the organization's ethical culture. Their actions and decisions set the tone for the rest of the organization.
- Employee Engagement: Engaging employees in cybersecurity compliance efforts fosters a sense of ownership and accountability. This can be achieved through regular communication, feedback mechanisms, and recognition programs.
Legal and Regulatory Compliance
Staying abreast of legal and regulatory requirements is essential for maintaining cybersecurity compliance. This involves continuous monitoring of regulatory changes and seeking legal counsel when necessary.
- Adhering to Laws: A fundamental aspect of a compliance program is ensuring that the organization complies with all relevant cybersecurity laws and regulations, including industry-specific regulations and general legal requirements.
- Regulatory Updates: Keeping up with regulatory updates helps stay informed about changes that may impact cybersecurity compliance. This involves monitoring regulatory bodies and industry associations.
- Legal Counsel: Seeking legal counsel provides expertise and guidance on complex cybersecurity issues. Legal professionals can help interpret regulations and develop compliance strategies.
Communication Strategies
Effective communication strategies are essential for promoting awareness and understanding of cybersecurity compliance requirements. Transparent communication fosters trust and encourages compliance.
- Transparent Communication: Maintaining open and transparent communication about cybersecurity policies and procedures helps build trust and credibility. This involves regular updates and clear messaging.
- Stakeholder Engagement: Engaging stakeholders, including employees, customers, and regulators, in cybersecurity efforts promotes a collaborative approach. This can be achieved through meetings, forums, and surveys.
- Regular Updates: Regular updates on cybersecurity matters keep everyone informed and engaged. This includes sharing information about regulatory changes, audit findings, and compliance initiatives.
Evaluation and Continuous Improvement
Continuous evaluation and improvement are vital for maintaining an effective cybersecurity compliance program. This involves assessing performance and making necessary adjustments to enhance the program.
- Performance Metrics: Establishing performance metrics helps evaluate the effectiveness of the cybersecurity compliance program. Metrics can include audit results, incident reports, and training completion rates.
- Feedback Loops: Creating feedback loops allows for continuous improvement based on input from employees, auditors, and other stakeholders. This involves collecting feedback, analyzing it, and implementing changes.
- Program Refinement: Refine the cybersecurity compliance program based on evaluation results to ensure it remains relevant and effective. This involves updating policies, procedures, and training programs.
Documentation and Recordkeeping
Maintaining accurate and accessible documentation is essential for cybersecurity compliance and accountability. Proper recordkeeping supports transparency and facilitates audits. Common challenges in achieving compliance.
- Documentation Standards: Establishing documentation standards helps maintain consistency and quality. This involves defining formats, templates, and storage protocols.
- Accessibility: Making cybersecurity documentation accessible to relevant stakeholders ensures they have the information needed to perform their roles effectively. This can be achieved through centralized document management systems.
The lack of clear guidance and inconsistent enforcement compound the challenge, leaving many organizations overwhelmed and unsure how to proceed.
Siloed Approach Within Organizations
One common obstacle in achieving cybersecurity compliance is the siloed approach within organizations. Departments may work in isolation, unaware of how their actions impact compliance efforts. This lack of collaboration can create blind spots and lead to gaps in policies and procedures that leave the organization vulnerable to non-compliance issues.
Resource Constraints
Resource constraints can hinder cybersecurity compliance initiatives, as dedicating time and budget to ensuring adherence to regulations may not always be seen as a top priority amidst competing business demands.
Summary
Cybersecurity compliance is a critical aspect of modern business operations. Organizations can protect their digital assets and maintain customer trust by understanding regulatory requirements, developing a robust compliance strategy, and adopting best practices. Continuous monitoring, risk management, and leveraging technology solutions are vital to achieving and sustaining compliance in an ever-evolving digital landscape.
FAQs
Cybersecurity compliance involves adhering to laws, regulations, and standards designed to protect sensitive information and ensure the integrity of organizational operations.
Organizations can ensure cybersecurity compliance by understanding relevant regulations, implementing robust security controls, conducting regular audits, and providing ongoing employee training. Utilizing technology solutions and involving key stakeholders in compliance efforts are also essential.
Non-compliance with cybersecurity regulations can result in severe consequences, including financial penalties, legal actions, reputational damage, and loss of customer trust. Organizations may also face operational disruptions and increased vulnerability to cyber threats.
Data protection laws, such as GDPR and CCPA, impose stringent requirements for handling personal data. These laws mandate measures to ensure data privacy, transparency, and accountability. Compliance with these laws is essential for protecting sensitive information and avoiding legal repercussions.
Employee training is crucial for cybersecurity compliance, as human error is a significant factor in security incidents. Regular training programs help employees understand security best practices, recognize potential threats, and respond appropriately to incidents, enhancing overall security posture.
Technology solutions, such as security tools, compliance management software, and automation technologies, can significantly enhance cybersecurity compliance. These solutions streamline documentation, monitoring, and reporting processes, reduce the risk of human error, and improve overall efficiency and effectiveness.
Strengthen cyber resilience with an integrated solution

A five-step approach to strengthen your company's cyber resilience, offering key benefits:
- Protect organizations from cyber disruptions
- Comply with cyber resilience regulations
- Align cyber resilience management with business objectives
- Maintain a proactive cyber resilience stance
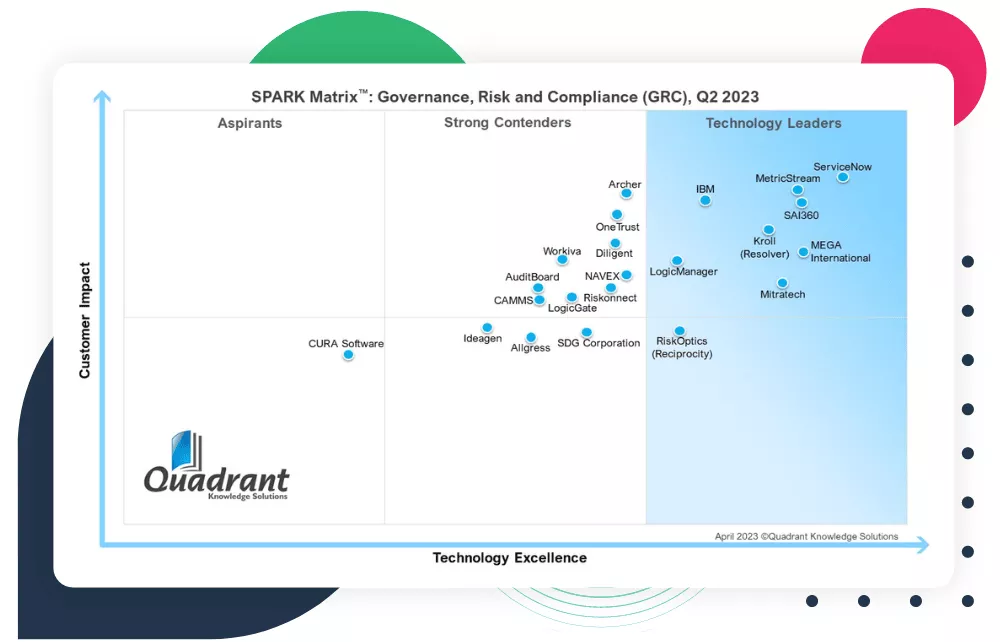
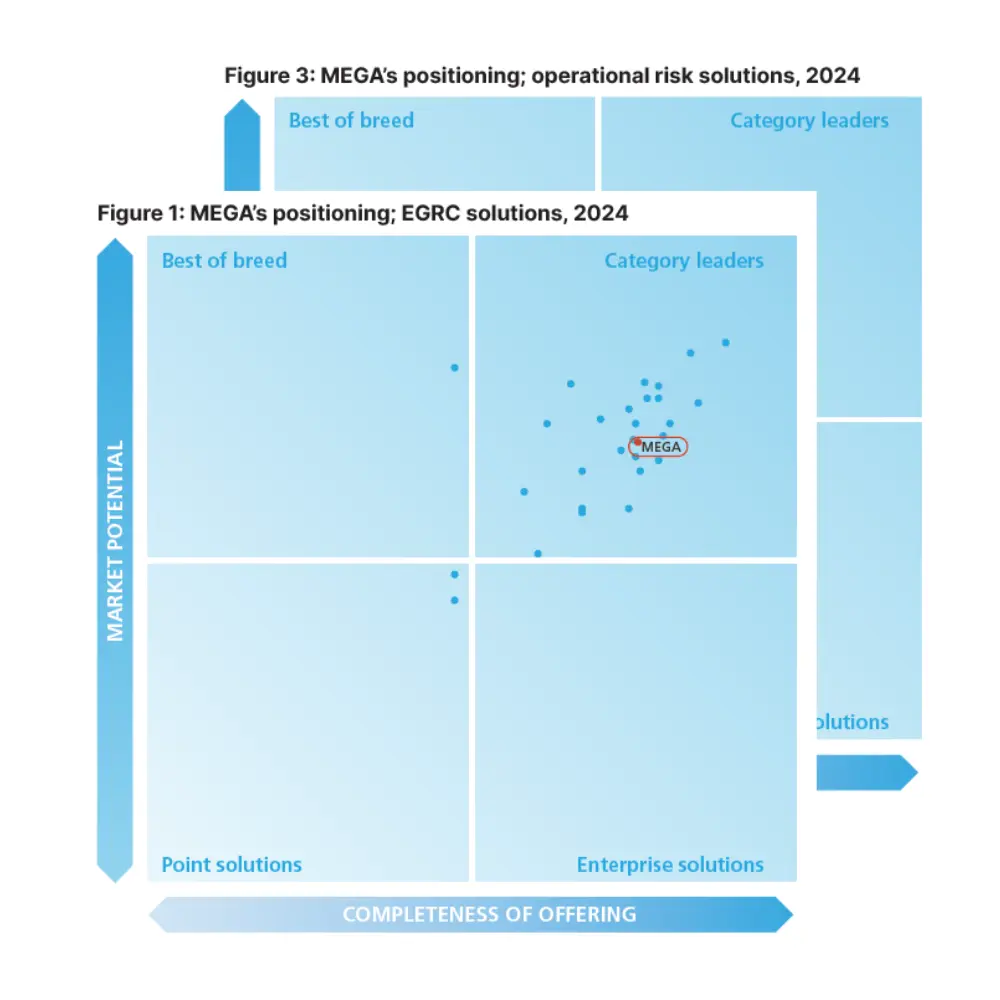
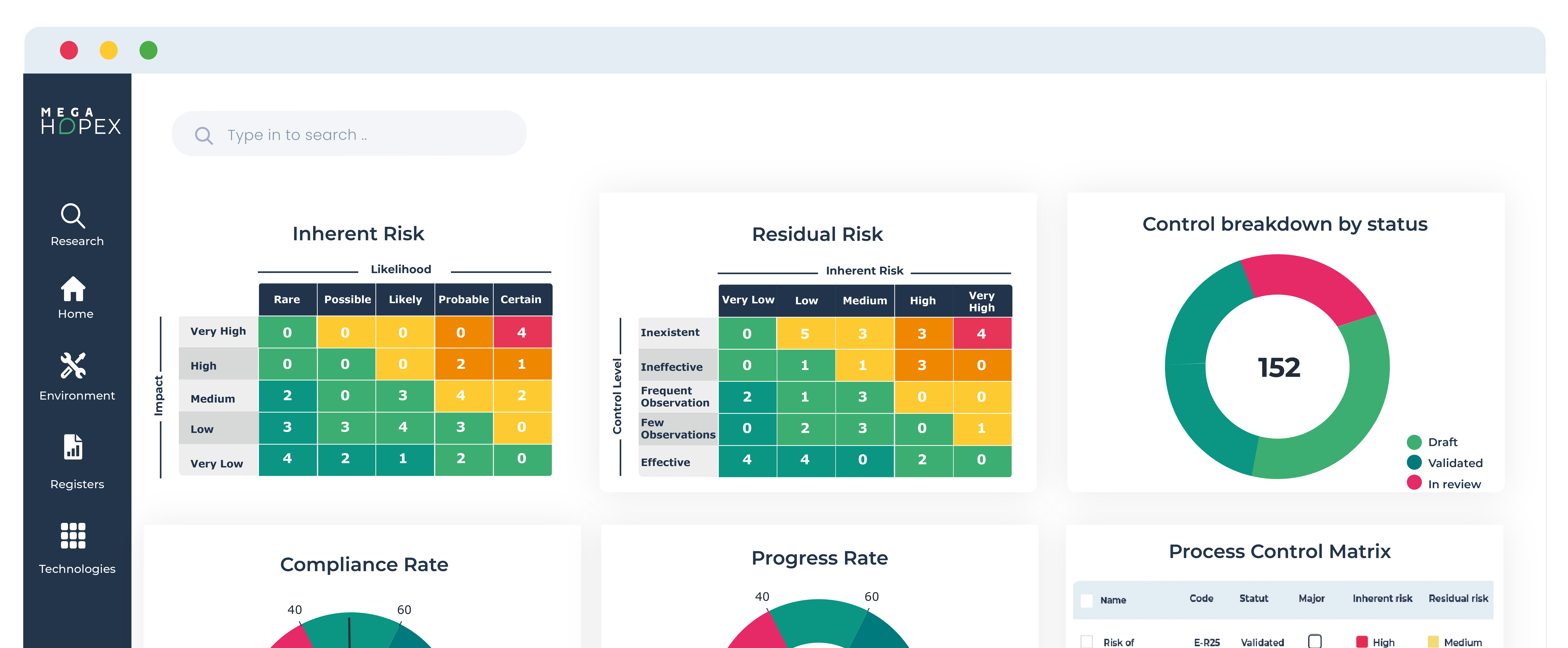
Governance, Risk and Compliance Related Content
Enhance operational resilience using integrated risk management
MEGA HOPEX for GRC
Request a demonstration of HOPEX for GRC, and see how you can have immediate value of your projects.