The four main principles of DORA Regulation: A Blueprint for Financial System Resilience
The European regulation known as DORA (Digital Operational Resilience Act) came into effect at the beginning of this year, with enforcement by all member states on January 17, 2025. By this date, financial participants, in the broadest sense, will have to meet new obligations organized in five pillars, designed to foster their digital resilience and the financial system as a whole. Given the proximity of this impending deadline, swift actions need to be taken today.
In 2008, the world was jolted by a financial crisis of unprecedented magnitude, surpassing the severity of past significant upheavals, such as the notorious Black Thursday of 1929. The global financial system, interwoven through intricate connections and dominated by influential players across multiple markets, succumbed to a domino effect where the collapse of one institution swiftly triggered the downfall of others. Today, the hyper-digitally connected world of financial institutions poses an even greater threat: should a key player's information system falter, the system's collapse could be near-instantaneous and of an unprecedented magnitude.
In this context, the Digital Operational Resilience Act (DORA) aims to guarantee the resilience of financial institutions and their associated third parties in a sector that is 100% digital and subject to constant cyber threats. DORA is a new EU regulation that mandates that companies and organizations in the financial sector manage all components of operational resilience: ability to protect, detect, contain, recover and repair ICT incidents.
In all, no fewer than 22,000 organizations will be impacted by this regulation.
To meet the obligations laid down by the DORA, financial institutions, and their third parties must implement and document a series of measures around their Information and Communication Technologies (ICT) which can be categorized into 4 main themes. By January 17, 2025, these 22,000 companies must ensure that all necessary preparations are in place to meet their obligations under these guidelines.
1 - Set up an ICT risk management system (Pillar 1)
The first pillar of the DORA is the most important: it serves as the foundation from which all other elements derive. It is also one of the most complex, as it requires a holistic approach based on a detailed knowledge of the company, its operations, and processes (especially the most critical ones), and above all its technological architecture (systems and applications supporting these processes).
Once this risk management system is in place, the DORA mandates a control obligation, which can be carried out continuously or at predefined frequencies. These highly detailed controls cover business and procedural aspects, as well as the technological layer - right down to the smallest application involved in a critical process. While most financial institutions already have such controls in place, it should be noted that IT controls specific to the DORA will be required to ensure full compliance with this new regulation.
In a broader sense, there will be a heightened need for closer collaboration between Risk and Control teams and the IT department.
2 - Identify and control third parties (Pillar 5)
Recognizing the growing complexity of financial information systems and its multitude of entities, applications, and infrastructures, the European regulator has broadened the scope of cautionary obligations to third-party services integrated within these architectures. This encompasses not only business partners who are inherently subject to the DORA, but also all technology partners.
Application publishers, cloud providers, and other Managed Services Providers (MSPs) will be impacted by the new European regulation. Specifically, regarding the terms of the Service Level Agreement (SLA) and the security they provide. Additionally, it will be crucial to establish contingency plans for substitute third parties in case of system failure or security breaches.
The concentration of services within a single third party can constitute a risk in itself: what happens if the main (or even only) cloud service provider is attacked? For this reason, it may be worthwhile for financial institutions to develop a multi-vendor strategy to limit the risks (and damage) in the event of an attack or a failure of a key third party.
3 - Regularly test your continuity capabilities (Pillar 3)
Risk awareness in the financial sector is nothing new. Business continuity and the threat of a domino effect have led most institutions to build contingency plans for their key processes. These are useful, if not vital solutions, provided they are regularly tested to ensure that they will continue to perform properly when situations take a turn for the worse.
Cybersecurity capabilities must be constantly tested and updated to counter the ever-evolving cyber threats. Cybersecurity is a living discipline requiring continual testing and updates in this relentless pursuit of protecting sensitive data and digital assets. For financial institutions, the imperative lies in establishing an ongoing investment plan and fostering genuine agility to uphold state-of-the-art cybersecurity systems to shield against the latest and most sophisticated malware.
4 - Report and share incidents (Pillar 2 and 4)
Finally, the DORA - in a similar manner to the RGPD regulation established a few years ago - imposes a new obligation for financial sector participants: maintain a comprehensive incident register serving as a reliable audit trail in the event of regulatory scrutiny. But not only that, in the event of a major incident, this register will serve as evidence that preventive actions were implemented proactively to ensure the IS's resistance and overall operational resilience.
At the same time, major incidents must be reported to the supervisory authorities. Beyond the identification of potential risks of propagation, the main aim is to build a knowledge base of cyberattacks, malicious acts, and threats. This knowledge base can then be shared with industry players to identify best practices that can be deployed to limit the impact of such threats.
This clear, easy-to-understand knowledge sharing also applies internally, by establishing a communication framework that can be understood by most employees. It's important to recognize that operational resilience is everyone's business. This holds true for key stakeholders such as Executive Management, the Risk Department (often merged with the Business Continuity Department), the Information Systems or Information Systems Security Department, and the Purchasing Department.
Although operational resilience and cyber security remain eminently technical in substance, the consequences of an incident extend well beyond the confines of the company, due to the potential ripple effect. The resilience of information systems and overall corporate resilience have emerged as highly strategic concerns that now find their way into executive committee discussions - even more so since, despite the technical nature of the subject, executives can be held criminally liable. So, better safe than sorry, and prepare for the January 2025 deadline.
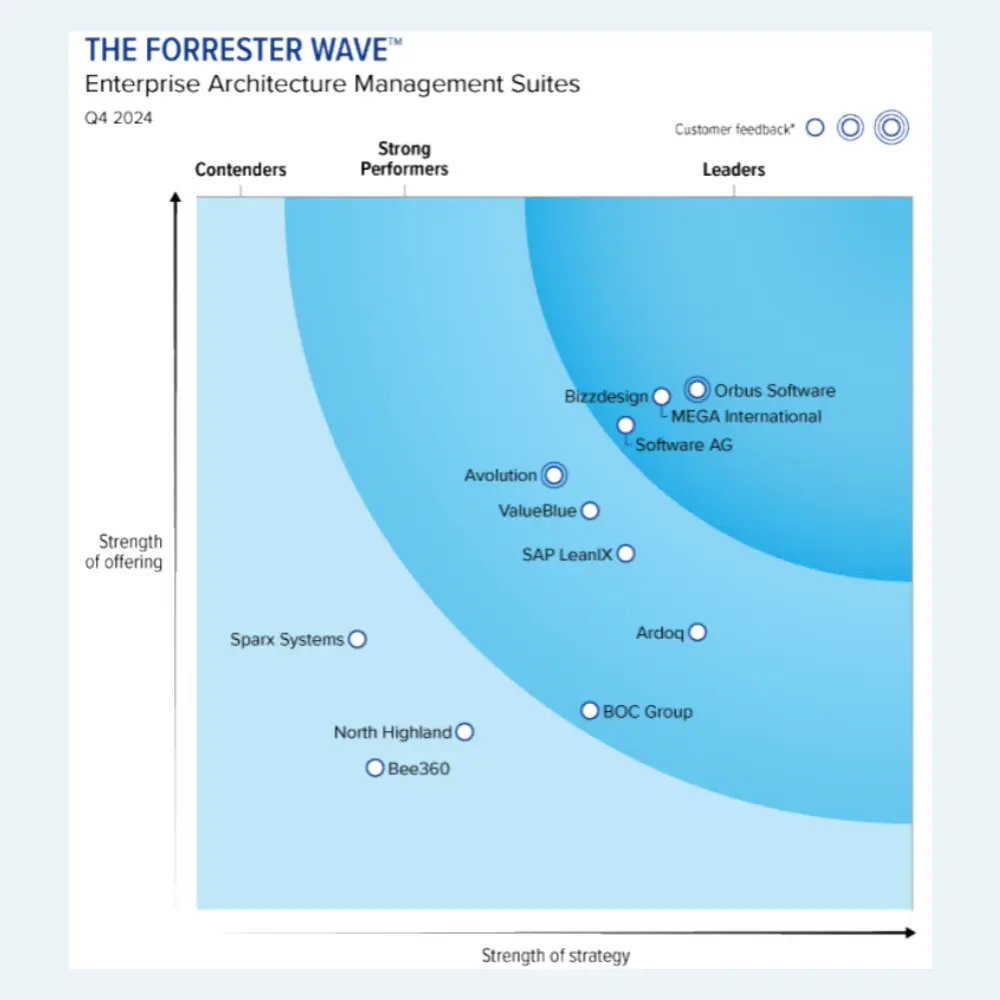
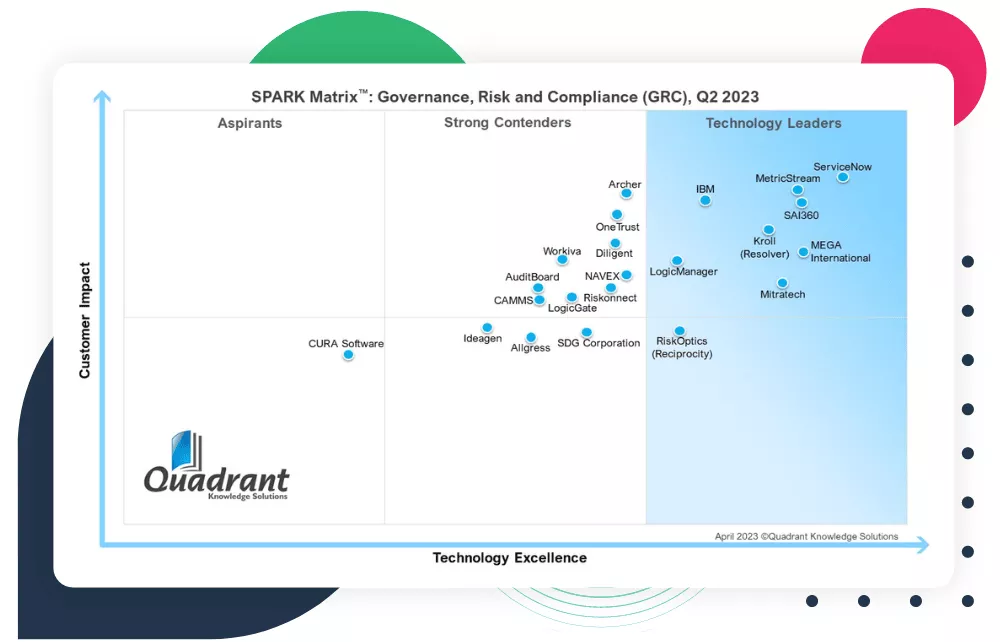
MEGA Leadership Related Content
See the Bigger Picture and Accelerate Business Value
Discover how organizations rely on us to transform their IT
Hear More From Companies Like Yours